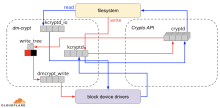
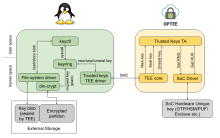
Cryptsetup is a utility used in Linux systems for setting up disk encryption using the Linux kernel's cryptographic modules. It primarily interacts with the Device Mapper subsystem to provide transparent disk encryption. Here are some key features of Cryptsetup:
1. LUKS (Linux Unified Key Setup): Cryptsetup supports LUKS, which is a standard on-disk format for storing encrypted volumes. LUKS provides a flexible and standardized way of handling key management for disk encryption.