It is a device-mapper target that provides transparent encryption of block devices. The term "dm" stands for device-mapper, which is a framework provided by the Linux kernel for creating virtual block devices.
With dm-crypt, you can encrypt entire block devices (such as hard drives or partitions) on-the-fly, meaning that the encryption and decryption processes are done in real-time as data is read from or written to the disk. This allows for the creation of encrypted volumes without the need to reformat the entire disk.
dm-crypt uses various encryption algorithms, such as AES (Advanced Encryption Standard), to secure the data on the disk. The encryption keys are typically derived from a passphrase or a key file. Users can unlock the encrypted device by providing the correct passphrase or key.
One common use of dm-crypt is to encrypt the root file system or other sensitive data on a Linux system to enhance security and protect against unauthorized access to data in case of theft or other security breaches. Additionally, it can be used to create encrypted containers or volumes within a larger storage device.
Key features of dm-crypt include:
- Transparent Encryption: dm-crypt encrypts and decrypts data on-the-fly as it is read from or written to the disk, providing seamless and transparent encryption for block devices.
- Support for Various Encryption Algorithms: dm-crypt supports a variety of encryption algorithms, including Advanced Encryption Standard (AES), Serpent, and Twofish. The choice of algorithm can be specified during the setup.
- Passphrase or Key File Authentication: Users can unlock encrypted devices by providing a passphrase or by using a key file. The encryption keys are derived from the passphrase or key file.
- Pluggable Hash Functions: dm-crypt allows the use of different hash functions for key derivation. Common hash functions include SHA-256 and SHA-512.
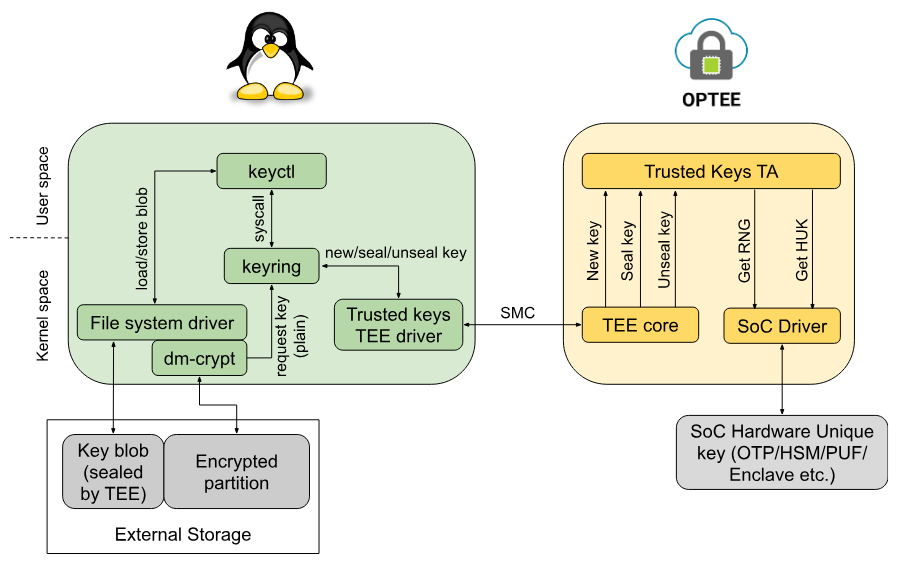
- Flexible Key Management: Keys used for encryption can be stored in kernel keyrings or managed using userspace tools. This flexibility allows for various key management strategies.
- Configurable Initialization Vectors (IVs): Initialization vectors are used to ensure that identical plaintext blocks encrypt to different ciphertext blocks. dm-crypt allows the use of different IV modes, such as plain, essiv (Essence of the Cipher Block Chaining In Linux), and others.
- Support for LUKS (Linux Unified Key Setup): LUKS is a standard for disk encryption that provides a platform-independent format for encrypted partitions. dm-crypt supports LUKS, allowing for compatibility across different systems.
- Integration with Cryptsetup: Cryptsetup is a userspace utility used to set up dm-crypt devices. It provides a convenient interface for creating, managing, and accessing encrypted volumes.
- Multi-Key Support: dm-crypt supports the use of multiple keys for a single device, allowing for more advanced access control and key management scenarios.
- Flexible Configuration: Users have the flexibility to configure various parameters during the setup of dm-crypt, including the encryption algorithm, key size, and other options.
Overall, dm-crypt is a powerful and flexible solution for disk encryption on Linux systems, providing a robust layer of security for sensitive data stored on block devices.

Comments