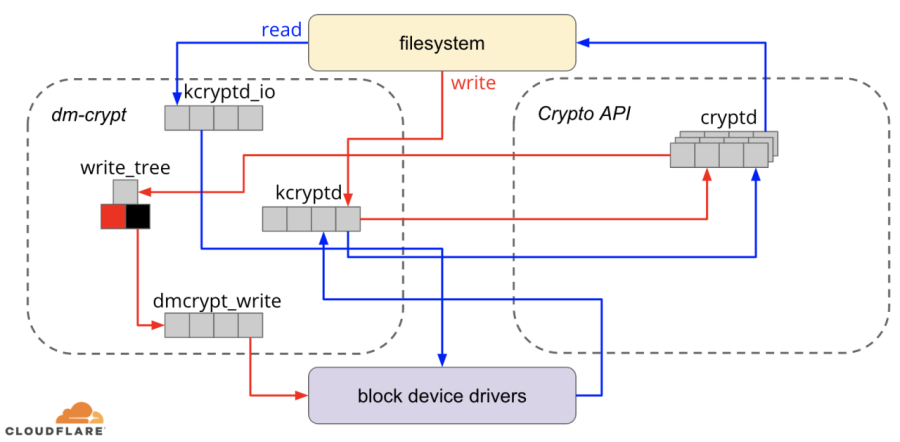
It primarily interacts with the Device Mapper subsystem to provide transparent disk encryption
Cryptsetup is a utility used in Linux systems for setting up disk encryption using the Linux kernel's cryptographic modules. It primarily interacts with the Device Mapper subsystem to provide transparent disk encryption. Here are some key features of Cryptsetup:
1. LUKS (Linux Unified Key Setup): Cryptsetup supports LUKS, which is a standard on-disk format for storing encrypted volumes. LUKS provides a flexible and standardized way of handling key management for disk encryption.
2. Multiple Encryption Algorithms: Cryptsetup supports various encryption algorithms, such as AES (Advanced Encryption Standard), Serpent, and Twofish. Users can choose the encryption algorithm based on their security and performance preferences.
3. User Password and Keyfile Support: Cryptsetup allows users to set up encryption using a passphrase, making it convenient for human users. Additionally, it supports the use of keyfiles for automated or scripted setups.
4. Key Slot Management: LUKS allows for the creation of multiple key slots, enabling the use of multiple passphrases or keyfiles. This feature is useful for key rotation or recovery scenarios.
5. Header Backup and Restore: Cryptsetup provides mechanisms to backup and restore LUKS headers, which contain critical information about the encryption setup. This is essential for data recovery and migration between systems.
6. Encryption and Decryption of Block Devices: Cryptsetup can be used to encrypt and decrypt entire block devices, such as hard drives or partitions. Once set up, the encryption is transparent to the user, who interacts with the device as if it were not encrypted.
7. Pluggable Hash and Encryption Modules: Cryptsetup supports the use of pluggable hash and encryption modules. This allows for flexibility in choosing specific cryptographic algorithms based on individual security requirements.
8. Integration with the Linux Unified Key Management (UKM) API: Cryptsetup can be integrated with the Linux Unified Key Management API to provide a centralized approach to key management, facilitating better integration with key management services.
9. Compatibility and Portability: Cryptsetup is widely used in various Linux distributions, ensuring compatibility and portability across different systems and environments.
10. Command-Line Interface: Cryptsetup is primarily used through the command line, making it scriptable and suitable for automation in system configuration.
11. Open Source: Cryptsetup is open source software, allowing users to inspect and modify the source code to meet specific requirements or contribute to its development.
Keep in mind that the features and capabilities of Cryptsetup may evolve over time as new versions are released, so it's a good idea to refer to the official documentation or release notes for the most up-to-date information.
