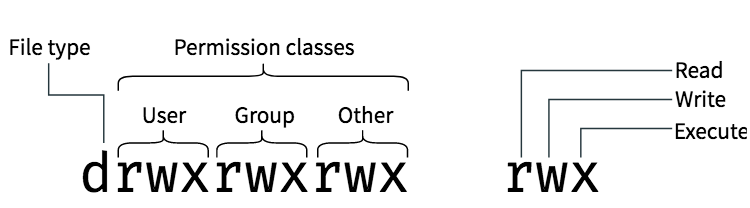
Filesystem is part of operating system to control and manage storing data on hard disk.
Filesystem permissions of Unix-like system are defined for three categories of affected users:
- The user who owns the file (u)
- Other users in the group which the file belongs to (g)
- All other users (o) also referred to as "world" and "everyone"
For the file, each corresponding permission allows following actions:
- The read (r) permission allows owner to examine contents of the file.
- The write (w) permission allows owner to modify the file.
- The execute (x) permission allows owner to run the file as a command.
For the directory, each corresponding permission allows following actions:
- The read (r) permission allows owner to list contents of the directory.
- The write (w) permission allows owner to add or remove files in the directory.
- The execute (x) permission allows owner to access files in the directory.
Here, the execute permission on a directory means not only to allow reading of files in that directory but also to allow viewing their attributes, such as the size and the modification time.
ls is used to display permission information (and more) for files and directories. When it is invoked with the "-l" option, it displays the following information in the order given.
- Type of file (first character)
- Access permission of the file (nine characters, consisting of three characters each for user, group, and other in this order)
- Number of hard links to the file
- Name of the user who owns the file
- Name of the group which the file belongs to
- Size of the file in characters (bytes)
- Date and time of the file (mtime)
- Name of the file
List of the first character of "ls -l" output
| character | meaning |
| - | normal file |
| d | directory |
| l | symlink |
| c | character device node |
| b | block device node |
| p | named pipe |
| s | socket |
chown is used from the root account to change the owner of the file. chgrp is used from the file's owner or root account to change the group of the file. chmod is used from the file's owner or root account to change file and directory access permissions. Basic syntax to manipulate a foo file is the following.
# chown
foo# chgrp
foo# chmod [ugoa][+-=][rwxXst][,...] fooFor example, you can make a directory tree to be owned by a user foo and shared by a group bar by the following.
# cd /some/location/# chown -R foo:bar .# chmod -R ug+rwX,o=rX .There are three more special permission bits.
- The set user ID bit (s or S instead of user's x)
- The set group ID bit (s or S instead of group's x)
- The sticky bit (t or T instead of other's x)
Here the output of "ls -l" for these bits is capitalized if execution bits hidden by these outputs are unset.
Setting set user ID on an executable file allows a user to execute the executable file with the owner ID of the file (for example root). Similarly, setting set group ID on an executable file allows a user to execute the executable file with the group ID of the file (for example root). Because these settings can cause security risks, enabling them requires extra caution.
Setting set group ID on a directory enables the BSD-like file creation scheme where all files created in the directory belong to the group of the directory.
Setting the sticky bit on a directory prevents a file in the directory from being removed by a user who is not the owner of the file. In order to secure contents of a file in world-writable directories such as "/tmp" or in group-writable directories, one must not only reset the write permission for the file but also set the sticky bit on the directory. Otherwise, the file can be removed and a new file can be created with the same name by any user who has write access to the directory.
Here are a few interesting examples of file permissions.
$ ls -l /etc/passwd /etc/shadow /dev/ppp /usr/sbin/exim4
crw------T 1 root root 108, 0 Oct 16 20:57 /dev/ppp
-rw-r--r-- 1 root root 2761 Aug 30 10:38 /etc/passwd
-rw-r----- 1 root shadow 1695 Aug 30 10:38 /etc/shadow
-rwsr-xr-x 1 root root 973824 Sep 23 20:04 /usr/sbin/exim4$ ls -ld /tmp /var/tmp /usr/local /var/mail /usr/src
drwxrwxrwt 14 root root 20480 Oct 16 21:25 /tmp
drwxrwsr-x 10 root staff 4096 Sep 29 22:50 /usr/local
drwxr-xr-x 10 root root 4096 Oct 11 00:28 /usr/src
drwxrwsr-x 2 root mail 4096 Oct 15 21:40 /var/mail
drwxrwxrwt 3 root root 4096 Oct 16 21:20 /var/tmpThere is an alternative numeric mode to describe file permissions with chmod. This numeric mode uses 3 to 4 digit wide octal (radix=8) numbers.
The numeric mode for file permissions in chmod commands
| digit | meaning |
| 1st optional digit | sum of set user ID (=4), set group ID (=2), and sticky bit (=1) |
| 2nd digit | sum of read (=4), write (=2), and execute (=1) permissions for user |
| 3rd digit | ditto for group |
| 4th digit | ditto for other |
This sounds complicated but it is actually quite simple. If you look at the first few (2-10) columns from "ls -l" command output and read it as a binary (radix=2) representation of file permissions ("-" being "0" and "rwx" being "1"), the last 3 digit of the numeric mode value should make sense as an octal (radix=8) representation of file permissions to you.
For example, try the following
$ touch foo bar
$ chmod u=rw,go=r foo
$ chmod 644 bar
$ ls -l foo bar
-rw-r--r-- 1 penguin penguin 0 Oct 16 21:39 bar
-rw-r--r-- 1 penguin penguin 0 Oct 16 21:35 fooTip: If you need to access information displayed by "ls -l" in shell script, you should use pertinent commands such as test, stat and readlink. The shell builtin such as "[" or "test" may be used too.
Backup Permissions
Getting backup or copy of the files on another volume formatted with Unix-like filesystems needs administration privilege so permissions will be changed to root after copying so definitely for the security reasons needs to change the permissions to user level whenever files are restored to home folder with the following solution:
Change restriction on folder and subfolders recursively Permission via executing:
sudo chmod -R ugo+rw foldernameOwnership via executing:
sudo chown -R username:groupname foldernameAlso
To change all the directories to 755 (drwxr-xr-x)
Via executing:
sudo find foldername -type d -exec chmod 755 {}\;To change all the files to 644 (-rw-r--r--)
Via executing:
sudo find foldername -type f -exec chmod 644 {}\;A journaling file system is a file system that maintains a special file called a journal that is used to repair any inconsistencies that occur as the result of an improper shutdown of a computer. Such shutdowns are usually due to an interruption of the power supply or to a software problem that cannot be resolved without a rebooting.
