The mentioned packages and applications here are recommended to get provided on every fresh installed operating system for many security reasons as follows:
OpenNTPD: a Unix daemon implementing the Network Time Protocol to synchronize the local clock of a computer system with remote NTP servers. It is also able to act as an NTP server to NTP-compatible clients.
OpenSSH: a suite of secure networking utilities based on the Secure Shell protocol, which provides a secure channel over an unsecured network in a client–server architecture.
OpenSMTPD: a Unix daemon implementing the Simple Mail Transfer Protocol to deliver messages on a local machine or to relay them to other SMTP servers.
OpenDNSSEC: a complete DNSSEC zone signing system which is very easy to use with stability and security in mind. There are a lot of details in signing zone files with DNSSEC and OpenDNSSEC covers most of it.
OpenSSL: a software library for applications that secure communications over computer networks against eavesdropping or need to identify the party at the other end. It is widely used by Internet servers, including the majority of HTTPS websites.
OpenVPN: an open-source commercial software that implements virtual private network techniques to create secure point-to-point or site-to-site connections in routed or bridged configurations and remote access facilities. It uses a custom security protocol that utilizes SSL/TLS for key exchange.
OpenConnect: an open-source software application for connecting to virtual private networks, which implement secure point-to-point connections. It was originally written as an open-source replacement for Cisco's proprietary AnyConnect SSL VPN client, which is supported by several Cisco routers.
Stunnel: an open-source multi-platform application used to provide a universal TLS/SSL tunneling service. Stunnel can be used to provide secure encrypted connections for clients or servers that do not speak TLS or SSL natively.
SCdaemon: GnuPG is GNU's tool for secure communication and data storage. It can be used to encrypt data and to create digital signatures. It includes an advanced key management facility and is compliant with the proposed OpenPGP Internet standard as described in RFC4880.
Installing the following extensions via package management:
network-manager-ssh
network management framework (SSH plugin core)
network-manager-pptp
network management framework (PPTP plugin core)
network-manager-l2tp
network management framework (L2TP plugin core)
network-manager-openvpn
network management framework (OpenVPN plugin core)
network-manager-openconnect
network management framework (OpenConnect plugin core)
network-manager-strongswan
network management framework (strongSwan plugin)
network-manager-vpnc
network management framework (VPNC plugin core)
Tor anonymity network and Privoxy non-caching system are configured already in Pars Enterprise Platforms whenever you decide to use these applications:
 |
 |
Tor Installation
Installing torbrowser-launcher torsocks obfs4proxy privoxy apt-transport-tor
net.inet.ip.random_id=1 >> /etc/sysctl.conf (FreeBSD)
tor_enable="YES" >> /etc/rc.conf (FreeBSD)
privoxy_enable="YES" >> /etc/rc.conf (FreeBSD)
Running an obfs4 bridge via Tor
Editing /etc/torrc (Linux) /usr/local/etc/torrc (FreeBSD) with Administration Privilege to:
#Bridge config RunAsDaemon 1 ORPort 9001 BridgeRelay 1 ServerTransportPlugin obfs4 exec /usr/bin/obfs4proxy ExtORPort auto #set the Nickname and Contact info ContactInfo info@example.tld Nickname username
or…..
UseBridges 1 ClientTransportPlugin obfs4 exec /usr/bin/obfs4proxy Bridge obfs4 89.163.181.170:443 A0D27B876F1DD14A15C223F48BD9CD4A6BC4517E cert=nOm4+38yOIZ+91ux/vMUOZjUv6pocGtPkZ1QUXumE03Y8akJmrdCwXzxvQVqVPLMlwQrXA iat-mode=0
Then you should get the bridge line. for get the bridge line go to https://bridges.torproject.org/ and get your bridge line.
Executing sudo service tor status
Executing sudo service tor restart
Privoxy and Tor for Increased Anonymity
Editing /etc/privoxy/config with Administration Privilege to:
forward-socks5t / 127.0.0.1:9050 .
Executing sudo service privoxy status
Executing sudo service privoxy restart
Tor Updating and Launching Issues
Executing gpg --homedir "$HOME/.local/share/torbrowser/gnupg_homedir/" --refresh-keys --keyserver pgp.mit.edu
Executing /home/pclite/.local/share/torbrowser/tbb/x86_64/tor-browser_en-US/Browser/start-tor-browser
Using Youtube-DL via Tor
Youtube-DL is a command line video downloader and the following commands make youtube-dl to download videos via Tor:
export http_proxy=socks5://127.0.0.1:9050 https_proxy=socks5://127.0.0.1:9050
and it can be disabled by unset http_proxy https_proxy
I2P is an anonymizing network, offering a simple layer that identity-sensitive applications can use to securely communicate. All data is wrapped with several layers of encryption, and the network is both distributed and dynamic, with no trusted parties.
I2pd: (I2P Daemon) is a full-featured C++ implementation of I2P client.
Installing i2p i2pd
i2p_enable="YES" >> /etc/rc.conf (FreeBSD)
i2p_user="i2p" >> /etc/rc.conf (FreeBSD)
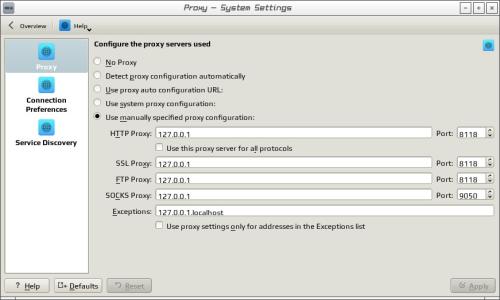
You may need to enable the network in KDE System Settings > Network Settings > Use manually specified proxy configuration >> Exceptions 127.0.0.1, localhost
KDE System Settings > Network Settings > Use Manually Specified Proxy Configuration > HTTP – SSL - FTP Proxy >> IP 127.0.0.1, Port 4444 (This will be Connected via I2P)
To work with Privoxy add the following line to the Privoxy configuration file: forward .i2p localhost:4444

Outproxy Terms Of Service
Remember: I2P was not designed for creating proxies to the outer Internet. Instead, it is meant to be used as an internal network.
The I2P project itself does not run any proxies to the Internet. The only outproxy is a service from the privacy solutions project. Consider donating to them for a continued stable service. Increased funding will allow them to improve this service.
http://privacysolutions.no
By default, I2P comes with two outproxies configured: false.i2p and outproxy-tor.meeh.i2p. Even the domain names are different, it's the same outproxy you hit. (multi-homed/keyed for better performance)
Filtering is active on these outproxies (for example, mibbit and torrent tracker access is blocked). Eepsites that are accessible via .i2p addresses are also not allowed via the outproxies. As a convenience, the outproxy blocks ad servers.
Tor is a good application to use as an outproxy to the Internet.
Comparison of Tor and I2P anonymizing proxy networks:
Tor - Onion Routing
Tor and Onion Routing are both anonymizing proxy networks, allowing people to tunnel out through their low latency mix network. The two primary differences between Tor / Onion-Routing and I2P are again related to differences in the threat model and the out-proxy design (though Tor supports hidden services as well). In addition, Tor takes the directory-based approach - providing a centralized point to manage the overall 'view' of the network, as well as gather and report statistics, as opposed to I2P's distributed network database and peer selection.
The I2P/Tor outproxy functionality does have a few substantial weaknesses against certain attackers - once the communication leaves the mixnet, global passive adversaries can more easily mount traffic analysis. In addition, the outproxies have access to the cleartext of the data transferred in both directions, and outproxies are prone to abuse, along with all of the other security issues we've come to know and love with normal Internet traffic.
However, many people don't need to worry about those situations, as they are outside their threat model. It is, also, outside I2P's (formal) functional scope (if people want to build outproxy functionality on top of an anonymous communication layer, they can). In fact, some I2P users currently take advantage of Tor to outproxy.
Comparison of Tor and I2P Terminology
While Tor and I2P are similar in many ways, much of the terminology is different.
| Tor network | I2P network |
| Cell | Message |
| Client | Router or Client |
| Circuit | Tunnel |
| Directory | NetDb |
| Directory Server | Floodfill Router |
| Entry Guards | Fast Peers |
| Entry Node | Inproxy |
| Exit Node | Outproxy |
| Hidden Service | Hidden Service, Eepsite or Destination |
| Hidden Service Descriptor | LeaseSet |
| Introduction point | Inbound Gateway |
| Node | Router |
| Onion Proxy | I2PTunnel Client (more or less) |
| Onion Service | Hidden Service, Eepsite or Destination |
| Relay | Router |
| Rendezvous Point | somewhat like Inbound Gateway + Outbound Endpoint |
| Router Descriptor | RouterInfo |
| Server | Router |
Benefits of Tor over I2P
Benefits of I2P over Tor
Open Menu > Preferences > Search > Default Search Engine >> DuckDuckGo
Open Menu > Add-ons Manager > Extensions >>
AdBlocker Ultimate
Free and improved AdBlocker. Completely remove ALL ads. No "acceptable" ads or whitelisted advertisers, block tracking and malware!
Cookie Quick Manager
A complete manager for cookies accumulated during browsing. It allows you to view, edit, create, delete, backup, restore cookies and search them by domain names. Contextual Identities such as Private Browsing, First-Party Isolation, and SameSite flag are also supported.
Disconnect
Make the web faster, more private, and more secure. Visualize and block the otherwise invisible websites that track your search and browsing history.
Flagfox
An extension that displays a flag icon indicating the current webserver's physical location. Knowing where you're connected to adds an extra layer of awareness to your browsing and can be useful to indicate the native languages and legal jurisdictions that may apply. Additional information can be obtained via a multitude of external lookups and users can add their own custom actions. All actions can be added to the flag icon's context menu and set to icon click or keyboard shortcuts for quick access.
FoxyProxy Standard
Easy to use advanced Proxy Management tool for everyone.
NoScript Security Suite
Maximum protection for your browser: NoScript allows active content only for trusted domains of your choice to prevent exploitation.
Plasma Integration
Multitask efficiently by controlling browser functions from the Plasma desktop.
Smart HTTPS
Helps you always use the secure HTTPS protocol, if supported by the site’s server. It automatically changes HTTP protocol to the secure HTTPS, and if loading errors occur, the extension will revert back to the original HTTP protocol.
User Agent Switcher
A highly customizable extension to spoof the User-Agent string of your browser with a new one globally, randomly or per hostname. You can alter your user-agent string to indicate you’re on a mobile device if you prefer seeing mobile versions of sites so they load quicker.
KeePassX: password manager or safe which helps you to manage your passwords in a secure way. You can put all your passwords in one database, which is locked with one master key or a key-disk. So you only have to remember one single master password or insert the key-disk to unlock the whole database. The databases are encrypted using the algorithms AES or Twofish.
FirewallConfig: firewalld is a dynamically managed firewall daemon with support for network/firewall zones to define the trust level of network connections or interfaces. It has support for IPv4, IPv6 firewall settings and for ethernet bridges and has a separation of runtime and persistent configuration options. It also provides a D-Bus interface for services or applications to add and apply firewall rules on-the-fly.
Wireshark: a network "sniffer" - a tool that captures and analyzes packets off the wire. Wireshark can decode too many protocols to list here.